Composr Tutorial: Using IP addresses to trace users
This tutorial focuses on IP addresses. A member-focused view is taken in the Policing a community site tutorial.
Tracing users (how IP addressing work)
Find your IP address
Computers often have more than one IP address
(one for each 'network interface', such as a network card or modem).
If you want to find your own IP address, as Composr sees it, hold the mouse over the 'Account' icon (person icon) in the top bar to find a tooltip containing the IP address – or use a third-party IP address reporting website.
Finding network settings
To find out about your network settings on Windows, type ipconfig /all at a command prompt.
On Linux or Mac, type ifconfig.
DNSstuff is a very useful website for looking into technical Internet related issues
An IP address is a 4 byte piece of data (typically, although the newer 6 byte standard has been forthcoming thing for many years now), represented usually in a human readable form of 4 numbers (0-255) separated by dots.
There are a number of different sources of IP addresses, however the decentralisation of the system can lead to abuse; these sources are:
- ISP (Internet service provider) assigned IP addresses, via DHCP. There is no specific pattern to these addresses. These are provided to computers when they, or their Internet router, sign on to the Internet via an ISP). This is the most usual source of IP addresses, and as these change, it can not be relied upon that a user will retain the same address for long; however, addresses usually are similar, and can be 'wildcarded' by the Composr IP ban feature. It is possible other users might at some point get that address, even though it is not very likely: if you place a ban on a wide range of addresses, such as 14.*.*.*, you are increasing the likelihood of a conflict to a dangerously high percentage, especially if an IP address belongs to a popular ISP.
- ISP (Internet service provider) assigned fixed IP addresses. Some ISPs provide these, often at additional cost. There is no specific pattern to these addresses.
- Local network IP address 10.0.*.* or 192.168.*.* type (non-routable [can't travel across the Internet] and open for anyone's local usage as it does not need to assigned by any authority, which means that something odd is happening if you find one of these).
- Localhost IP address, 127.0.0.1. If you see this, then the request came from the server, or the IP address was added to the Composr database arbitrarily by some code because the true one was not known (often importers do this).
Finding a domain's IP address
To find out what your computer thinks the IP address of an Internet server is, type:
nslookup <server-domain-name>
at a command prompt.
There is a major problem with identifying users by IP address, and that is one of proxy s and gateway s (also known as, NAT [network address translation]). If a network is 'behind' a server that makes Internet requests on their behalf, and relays information back using its own internal algorithms, then all users of this server may be seen under a single IP address. Composr will try and detect the 'true' IP address, based on the information available, but we cannot guarantee this will be the case. AOL is renowned for using proxy servers, and will particularly jump rapidly between IP addresses when the AOL browser is used. For the gateway case, it is more than likely that a large school, for example, would use a gateway, rather than exposing all school computers to the Internet via their own IP addresses (in this sense, a NAT/gateway is a form of firewall).
Composr tracking
Composr tracks IP addresses in a number of ways:- When a guest makes a post on Conversr , the IP address is viewable by putting the mouse over the listed name of the guest poster (where the username of a real member usually resides). If you click it, it'll do an investigate-user operation on the IP address
- For every page view, the IP address of the page viewer is stored. This allows detection of what areas of the site a viewer has visited, and in what order
- Whenever a submission is made, the IP address is stored. The submitter banning management screen shows these IP addresses in its drop-down list
Tools
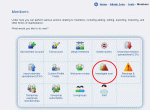
Composr provides modules (screenshots below) for working with the collected data, and settings:- The 'Investigate user' module is the main tool for finding information about an IP address (access it from Admin Zone > Tools > Members > Investigate user)
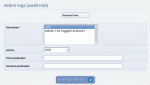
- The 'Action Logs' module (access it from the Admin Zone > Audit > Actions logs) can be used to quickly find out information from a submit that wasn't immediately available (for example, if a user submitted something without being logged-in and hence was not identified, but if by an IP address scan, they were in fact identifiable). The module can also be used to ban or unban a submitter, based on both member (prevents the member submitting again) and IP address (prevents the IP address being used to access the site)
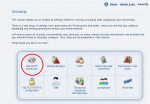
- The 'Banned IP addresses' (access it from Admin Zone > Security > Banned IP addresses) module can be used to enter IP addresses for banning, along with free-form notes
Tools available in the Admin Zone Audit Section
Tools available in the Admin Zone security section
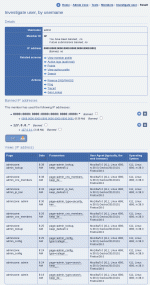
Investigating a user
Choosing a member to view the action logs of
Managing banned IP addresses
Note that banned IP addresses are restricted from accessing Composr from a very earlier point. If the .htaccess file is available and writable (Apache-only) then the bans are written in here so that PHP doesn't even need to initialise for a ban to be detected.
Other kinds of banning
Composr (Conversr ) does also support many other types of banning, and other punitive tools. See the Policing a community site tutorial for more information.A closer look at the Investigate User module
Options available during an investigation
Starting an investigation
Composr has tried to pull together as much as it can, by trying to match against the triad of IP address, member ID, and username/author. Links are provided that correspond to each of these, each link providing a different perspective on what is likely a single user.
If you would like to provide a low-level ban against IP address it is advisable to carefully research the usages of each IP address set by performing additional IP-based lookups (following the IP addresses as linked will lead you to do this).
These tools are:
- Reverse-DNS lookup - this will find try and find a domain name attached to the IP address.
- DNS lookup - this will find try and find a domain name attached to the IP address, and then the IP address attached to the domain name: with a second IP address, further analysis might be performed
- WHOIS query - this will try and find a domain name attached to the IP address, and then try to find real-world details about the registered owner of that domain name
- Ping - this will see if the computer with the IP address responds to ‘pings’; servers often will, but desktop computers rarely will
- Tracert - this will find the network route between the server that provides this web tool, and the server of the IP address; it provides an impression of the locality and connectivity of the associated computer
- Geo-lookup - this will try and find the geographical location of the IP address; it can be widely inaccurate however: for example, in the past UK AOL users have been shown as being located in the US
Concepts
- IP address
- Every computer connected to the Internet has an IP address of its own, although the IP address may change if that computer has 'rented' it via DHCP
- DHCP
- Dynamic Host Configuration Protocol: a protocol that hands out IP addresses to computers on a network (including those connecting to the Internet), often arbitrarily
- ISP
- An Internet Service Provider
- Gateway
- A gateway routes packets between one network to another (e.g. between a network and the Internet) via NAT
- NAT
- Network Address Translation. NAT allows two networks to communicate with IP addresses that a normal router could not have joined together
- Firewall
- A computer/box that limits network traffic between networks; some firewalls are also routers
- Proxy
- A proxy server allows computers on a network to connect to the Internet via special proxy server protocols that encapsulate requests; the proxy server then decodes and executes them, relaying the results
- Router
- A router joins two networks; non-gateway routers actually join the networks such that all computers on a network being joined with the Internet become a part of the Internet themselves
See also
- Security
- Policing a community site
- Basic forum moderation
- Composr member system
- Legal and social responsibilities
- Anti-spam settings
- How the Internet actually works
Feedback
Have a suggestion? Report an issue on the tracker.