Composr Tutorial: Integrating Composr into a corporate network via LDAP
Written by Chris Graham (ocProducts)
If you plan to integrate your website into a corporate network, perhaps as your intranet, you may wish to use the same credentials for users of the website as you do for your other services, such as desktop login. With this approach, there are a number of advantages:- There is no issue with preventing non-authorised users joining, or having to manually validate accounts of those who do join.
- Users do not need to join.
- A user only has a single password to maintain.
- It is clear who the users of the website are, as there is no potential for them to use unknown handles.
- Usergroup membership is the same as on your corporate network, and permissions can be assigned using it.
The standard protocol for sharing of network credentials is called LDAP . Two variations of LDAP are supported:
- Active Directory , which is a standard part of the Windows architecture.
- OpenLDAP , which is the de-facto standard for Linux systems.
LDAP support is not regularly tested. If you find any clear bugs please report them to the developers, and they will be rectified in a timely manner. If you're not sure what settings to use then you'll probably need someone with programming experience to step through it all, as LDAP can be very complex and involve non-standard/diverse schema.
Configuring
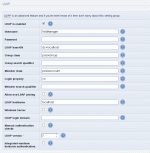
Configuring LDAP support
LDAP is known as a directory service , and in theory, all the LDAP servers of the world together form a combined directory. Because of this, each LDAP server is given a position in the directory, specified in the LDAP DN (directory navigation) syntax; this is known as the base-DN, and the system administrator of the network should be able to identify this. The base-DN is usually based on the DNS domain name of the network the LDAP server serves, for example: dc=intranet,dc=example,dc=com might be used for the domain intranet.example.com. It is important to use the DNS of the domain and not the DNS of the server on the domain.
When LDAP is working, login is a snap
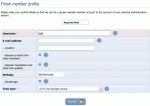
After logging in for the first time, Composr will ask for some details to be finalised
The LDAP standard is more concerned with protocol and structure than the actual schema used to hold information. Therefore there are significant differences between implementations, and thus we must consider each a separate case.
Active Directory
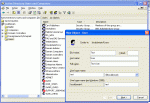
Adding a user to Active Directory
As Active Directory is so standard across Windows, Composr has good support for its schema.
The usergroup, 'Administrators' is mapped to the Composr Administrators usergroup.
The usergroup, 'Users' is mapped to the lowest ranking Composr member usergroup.
OpenLDAP
Composr supports the NIS (aka POSIX ) schema. This is the schema that is installed on the server in order for Linux clients to be able to login using the LDAP database for full credentials. It is possible that there are variations of the schema installed on different networks, therefore it may be necessary to ask a professional developer to make sure Composr can handle your specific configuration.The usergroups, 'root' and 'admin', are mapped to the Composr Administrators usergroup. The usergroup, 'users' is mapped to the lowest ranking Composr member usergroup.
Changed Composr behaviour
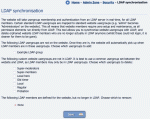
Synchronising with LDAP (Composr doesn't duplicate LDAP information, but some parameters need to be set and clean-ups undertaken, which this tool assists)
- Automatic mapping between the standard Composr usergroups and LDAP usergroups will be performed, even when the names do not quite correlate. For example, an administrator in LDAP, will be an administrator in Composr, automatically.
- Unless you allow it, joining on Composr will be disabled, in favour of only allowing new LDAP accounts to be seen. Composr assumes all LDAP account management is done elsewhere, and only employs read-only access to the LDAP data.
- It is necessary to use the LDAP synchronisation module to choose which LDAP usergroups will be featured in Composr. This is done for reasons of cleanliness: often an LDAP database will consist of many cryptic usergroups that would look out-of-place on the portal. Do this from Admin Zone > Security > LDAP.
- When an LDAP user logs in for the first time, Composr will ask for some supplementary information them (such as their e-mail address) in order to complete the Composr profile. This is because usually LDAP does not hold this data, but Composr requires it.
- Passwords and usernames of LDAP users cannot be changed.
- LDAP users may not change their usergroup membership from within Composr.
- The 'lost password' feature will not work for LDAP users.
Concepts
- LDAP
- Lightweight Directory Access Protocol; a scheme that allows many systems to share authentication and user profile information
- OpenLDAP
- An Open Source LDAP system
- Active Directory
- The Windows Server LDAP system
- NIS
- Network information system; the traditional network based authentication scheme used on Linux, to which OpenLDAP/Linux work to for Linux authentication
- POSIX
- A standardisation effort for Unix/Linux that has an implication for users and usergroups
- Domain Controller
- A Windows Server that manages authentication for a Windows Domain (a contained Windows network)
- Directory service
- A service available on a network for looking up entries in a directory. LDAP is an example of a protocol to provide a directory service: a directory that is most often of users
See also
Feedback
Please rate this tutorial:
Have a suggestion? Report an issue on the tracker.